Getting Started with the i.MX 8XLite Evaluation Kit Board
本文档内容
-
Out of the Box
-
Get Software
-
Configure Software
1. Out of the Box
The following section describes the steps to boot the i.MX 8XLite EVK.
Development kit contains:
- i.MX 8XLite EVK board for smart devices
- USB cable (micro-B to standard-A)
- Cable -Assembly, USB 2.0 Type-A male, USB Type-C male, shielded, 1m
- 12 V/8.3 A universal power supply
- Wi-fi M.2 module
- 16 GB SD card with bootable operating system demonstration image
1.2 Insert the SD Card (J6)
The kit includes an SD card with a pre-built NXP Linux binary demo image. Without modifying the binary inside the SD card, booting from this SD card provides a default system with certain features for building other applications on top of Linux. The software is described in the following sections.
1.3 Connect USB Debug Cable
Connect the micro-B end of the supplied USB cable into Debug UART port
J19. Connect the other end of the cable to a host computer.
If you are not sure about how to use a terminal application, try one of the following tutorials depending on the operating system of the host machine: Minicom Tutorial, Tera Term Tutorial, PuTTY Tutorial.
1.4 Connect Power Supply
Connect the power supply cable to the power connector (J1).
The processor starts executing from the on-chip ROM code. With the default boot switch setup, the code reads the fuses to define the media where it is expected to have a bootable image. After it finds a bootable image, the U-Boot execution should begin automatically.
Information is printed in the serial console for the Arm® Cortex®-A35. If you do not stop the U-Boot process, it continues to boot the kernel.
2. Get Software
2.1 Embedded Linux®
This section is applicable ONLY if attempting to load a Linux operating system on the board.
The i.MX Linux board support package (BSP) is a collection of binary files, source code and support files that are used to boot an Embedded Linux image on a specific i.MX development platform.
Current releases of Linux binary demo files can be found on the i.MX Linux download page. Additional documentation is available in the i.MX Linux documentation bundle under the Linux sections of the i.MX Software and Development Tool.
2.2 Overview
Before the Linux OS kernel can boot on an i.MX board, the Linux kernel is loaded to a boot device (SD card, eMMC and so on) and the boot switches are set to boot that device.
There are various ways to download the Linux BSP image for different boards and boot devices.
For this getting started guide, only a few methods to transfer the Linux BSP image to an SD card are listed. Experienced Linux developers can explore other options.
2.3 Download an NXP Linux BSP Pre-built Image
The latest pre-built images for the i.MX 8XLite EVK are available on the Linux download page under the most current version on Linux.
The pre-built NXP Linux binary demo image provides a typical system and basic set of features for using and evaluating the processor. Without modifying the system, the users can evaluate hardware interfaces, test SoC features, and run user space applications.
When more flexibility is desired, an SD card can be loaded with individual components (boot loader, kernel, dtb file, and rootfs file) one-by-one or the .sdcard image is loaded and the individual parts are overwritten with the specific components.
Install UUU on Linux® Distro
Install UUU on Linux Distro
Download the atest stable files from UUU GitHub page. An extensive tutorial for UUU can be found in UUU GitHub page.
uuulibusb1(via apt-get or any other package manager)
Burn the NXP Linux BSP Image to the Board
By default, this procedure flashes the image to the eMMC flash. Check the UUU GitHub page for reference on how to flash the image to other devices.
Open a terminal application and change directory to the location where uuu and the latest Linux distribution for i.MX 8XLite EVK are located. Add execution permission to the uuu file and execute it. Uuu waits for the USB device to connect
1$ chmod a+x uuu1$ sudo ./uuu <kernel_version>_images_<SOC>.zipTurn on the board, uuu starts to copy the images to the board.
When it finishes, turn off the board, and consult Boot switch setup to configure the board to boot from eMMC.
Install UUU on Windows™
Download the latest stable files from UUU GitHub page. An extensive tutorial for UUU can be found in UUU GitHub page.
uuu.exe- Serial USB drivers (depending on your board and Windows installation - check Windows Device Manager)
Burn the NXP Linux BSP Image to the Board
By default, this procedure flashes the image to the eMMC flash. Check the UUU GitHub page for reference on how to flash the image to other devices.
Open the command prompt application and navigate to the directory where the uuu.exe file and the Linux release for the i.MX 8XLite EVK are located.
1uuu.exe <kernel_version>_images_<SOC>.zipTurn on the board, uuu starts to copy the images to the board.
When it finishes, turn off the board, and consult Boot switch setup to configure the board to boot from eMMC
3. Configure Software
3.1 MCUXpresso SDK
The MCUXpresso Software Development Kit (MCUXpresso SDK) provides comprehensive software source code to be executed in the i.MX 8DualXlite M4 core.
If you do not wish to enable the Arm® Cortex®-M4 on i.MX 8DualXLite at this moment you can skip this section.
3.2 Overview
The MCUXpresso SDK is designed for the development of embedded applications for Arm Cortex-M4 standalone or collaborative use with the A cores. Along with the peripheral drivers, the MCUXpresso SDK provides an extensive and rich set of example applications covering everything from basic peripheral use case examples to demo applications. The MCUXpresso SDK also contains RTOS kernels, and device stack, and various other middleware to support rapid development.
Depending on the OS used in the host machine, the way to build and deploy the demos can vary. Choose an option below for detailed instructions:
Linux®
Download MCUXpresso SDK on Linux
Current releases of the MCUXpresso SDK and source code can be found at MCUXpresso SDK Builder.
To download the MCUXpresso SDK for i.MX 8DualXLite, follow these steps:
- Click on “Select Development Board”.
- Select
EVK-MIMX8DXLunder “Select a Device, Board, or Kit” and click on “Build MCUXpresso SDK” on the right.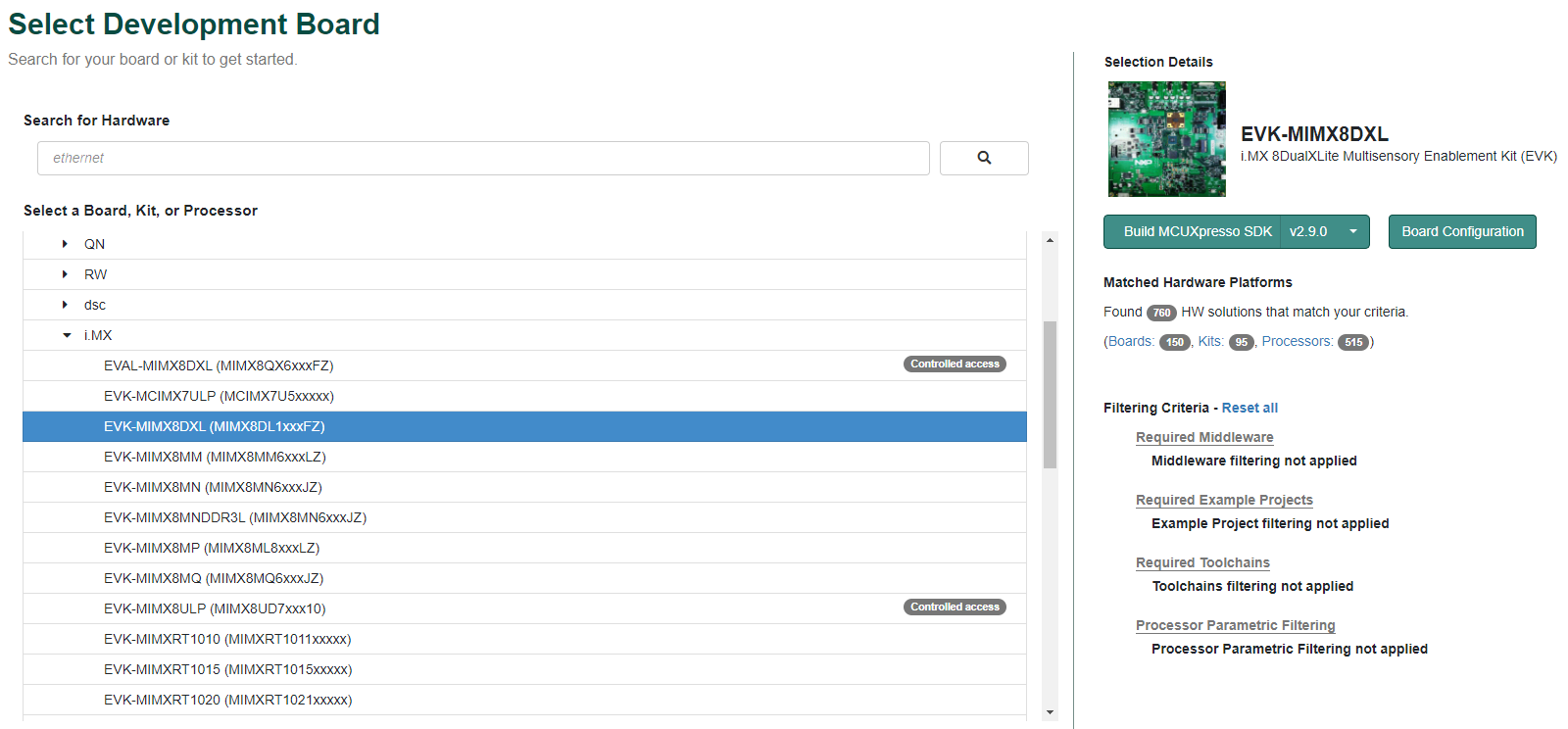
- Select “Host OS” as Linux.
- Select “Toolchain/IDE” as GCC ARM Embedded.
- Click on “Select Optional Middleware“, “Select All“ and hit “Save changes“.
- Click on “Download SDK”.
- Wait for the SDK to build and download the package.
Install toolchain
- Download and run the installer from
launchpad.net/gcc-arm-embedded. This is the actual toolchain. The toolchain includes the compiler, linker, and so on. The GCC toolchain should correspond to the latest supported version, as described in the MCUXpresso SDK Release Notes found in the package already downloaded. -
Export the toolchain location as
ARMGCC_DIR.1
$ export ARMGCC_DIR=/usr - Ensure that cmake is installed:
1
$ sudo apt-get install cmake1
$ sudo apt-get install gcc-arm-none-eabi
Build MCUXpresso SDK
- Change the directory of the command window to the demo armgcc directory and run the build command:
1
$ cd <install_dir>/boards/EVK-MIMX8DXL/demo_apps<demo_name>/armgcc1
$ ./build_all.sh -
There are two project configurations (build targets) supported for each MCUXpresso SDK project:
Debug
Compiler optimization is set to low, and debug information is generated for the executable. This target is selected for development and debug.
Release
Compiler optimization is set to high, and debug information is not generated. This target is selected for final application deployment.
Note
There are script files provided to build both configurations. For this example, the
Debugtarget is built andbuild_debug.shis typed on the command line. If theReleasetarget is desired, typebuild_release.shinstead. - The previous command generates the debug and release binaries (
.bin). These files are in the debug and release folders. - Copy the bootable image
hello_world.binto the boot partition of the SD card.
Run Applications Using U-Boot
This section describes how to run applications using an SD card and pre-built U-Boot image for i.MX processor.
- Following the steps on the Embedded Linux® tab, prepare an SD card with a pre-built U-Boot + Linux image from Linux BSP package for the i.MX 8DualXLite processor. If you have already loaded the SD card with a Linux image, you can skip this step.
- Insert the SD card in the host computer (Linux or Windows), and copy the application image (for example
hello_world.bin) to the FAT partition of the SD card. - Safely remove the SD card from the PC.
- Insert the SD card to the target board. Make sure to use the default boot SD slot and double check the [Boot Switch Setup]. The default configuration of the validation board boots from
J12, and on MEK board there is only one SD slot which is used for boot. - Connect the DEBUG UART slot on the board with to the PC through the USB cable. The Windows OS installs the USB driver automatically, and the Ubuntu OS will find the serial devices as well. See [Serial Communication Console setup] section in Out of box for more instructions on serial communication applications.
- Open a second terminal emulator on the i.MX 8XLite EVK board's second enumerated serial port. This is the Cortex®-M4's serial console. Set the speed to 115200 bit/s, data bits 8, no parity, and power on the board.
-
Power up the board and stop the boot process by pressing any key before the U-Boot countdown reaches zero. At the U-Boot prompt on the first terminal emulator, type the following commands to U-Boot.
123
=>fatload mmc 1:1 0x88000000 hello_world.bin => dcache flush => bootaux 0x88000000
Windows™
Download MCUXpresso SDK on Windows
Current releases of the MCUXpresso SDK and source code can be found at MCUXpresso SDK Builder.
To download the MCUXpresso SDK for i.MX 8DualXLite, follow these steps:
- Click on “Select Development Board”.
- Select
EVK-MIMX8DXLunder “Select a Device, Board, or Kit” and click on “Build MCUXpresso SDK” on the right.
- Select “Host OS” as Windows.
- Select “Toolchain/IDE” as
GCC ARM Embedded. - Click on “Select Optional Middleware“, “Select All“ and hit “Save changes“.
- Click on “Download SDK”.
- Wait for the SDK to build and download the package.
Install Toolchain
Download and run the installer from GNU Arm Embedded Toolchain. This is the actual toolchain. The toolchain includes the compiler, linker, and so on. The GCC toolchain should correspond to the latest supported version, as described in the MCUXpresso SDK Release Notes found in the package already downloaded.
Install MinGW
The Minimalist GNU for Windows (MinGW) development tools provide a set of tools not dependent on third-party C-Runtime DLLs (such as Cygwin). The build environment used by the MCUXpresso SDK does not utilize the MinGW build tools, but does leverage the base install of both MinGW and MSYS. MSYS provides a basic shell with a Unix-like interface and tools.
- Download the latest MinGW mingw-get-setup installer from: MinGW - Minimalist GNU for Windows Files
- Run the installer. The recommended installation path is C:\MinGW, however, you may install to any location.
-
Ensure that the
mingw32-baseandmsys-baseare selected under Basic Setup.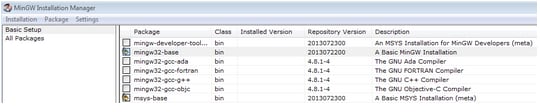
-
Click
Apply Changesin the Installation menu and follow the remaining instructions to complete the installation.
-
Add the appropriate item to the Windows operating system PATH environment variable. It can be found under Control Panel → System and Security → System → Advanced System Settings in the Environment Variables… section. The path is:
1
<mingw_install_dir>\binImportant
Assuming the default installation path,
C:\MinGW, an example is shown below. If the path is not set correctly, the toolchain does not work.If you have
C:\MinGW\msys\x.x\binin thePATHvariable (as required by KSDK 1.0.0), remove it to ensure that the new GCC build system works correctly. -
Create a system environment variable and name it
ARMGCC_DIR. The value of this variable should point to the Arm® GCC Embedded tool chain installation path, which, for this example, is:1
C:\Program Files (x86)\GNU Tools Arm Embedded\4.8 2014q3Reference the installation folder of the GNU Arm® GCC Embedded tools for the exact pathname of the installation.

Install CMake
- Download CMake 3.0.x from Get CMake
-
Before installing CMake, ensure that the option Add CMake to system PATH is selected. It is up to the user to select whether it is installed into the PATH for all users or just the current user. In this example, the assumption is that it is installed for all users.
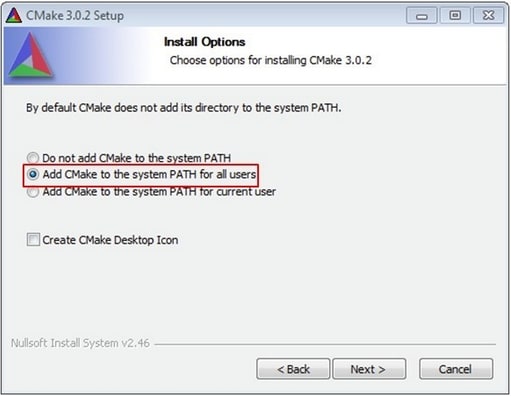
- Follow the remaining instructions of the installer.
Build MCUXpresso SDK
-
Open a GCC Arm® Embedded tool chain command window. To launch the window, from the Windows operating system Start menu, go to Programs → GNU Tools Arm Embedded <version> and select GCC Command Prompt.

-
Change the directory of the command window to the demo armgcc directory and run the build command:
1
> cd <install_dir>\boards\ EVK-MIMX8DXL\demo_apps<demo_name>\armgcc1
> build_all.batOr double-click on the
build_all.batfile in Explorer to perform the build. The expected output is shown in this figure: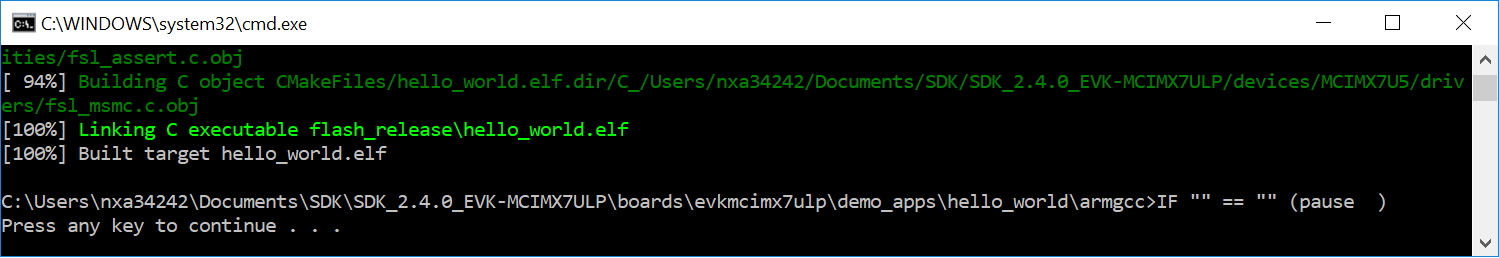
-
There are two project configurations (build targets) supported for each MCUXpresso SDK project:
Debug
Compiler optimization is set to low, and debug information is generated for the executable. This target is selected for development and debug.
Release
Compiler optimization is set to high, and debug information is not generated. This target is selected for final application deployment.
Note
There are script files provided to build both configurations. For this example, the Debug target is built and
build_debug.batis typed on the command line. If theReleasetarget is desired, typebuild_release.batinstead. - The previous command generates the debug and release binaries (
.bin). These files are in the debug and release folders. - Copy the bootable image
hello_world.binto the boot partition of the SD card.
Run applications Using U-Boot
This section describes how to run applications using an SD card and pre-built U-Boot image for i.MX processor.
- Following the steps on the Embedded Linux® tab, prepare an SD card with a pre-built U-Boot + Linux image from Linux BSP package for the i.MX 8DualXLite processor. If you have already loaded the SD card with a Linux image, you can skip this step.
- Insert the SD card in the host computer (Linux or Windows), and copy the application image (for example hello_world.bin) to the FAT partition of the SD card.
- Safely remove the SD card from the PC.
- Insert the SD card to the target board. Make sure to use the default boot SD slot and double check the [Boot Switch Setup]. The default configuration of the validation board boots from J12, and on MEK board there is only one SD slot which is used for boot.
-
Connect the DEBUG UART slot on the board with to the PC through the USB cable. The Windows OS installs the USB driver automatically, and the Ubuntu OS will find the serial devices as well.
See [Serial Communication Console setup] section in Out of box for more instructions on serial communication applications.
- Open a second terminal emulator on the i.MX 8XLite EVK board's second enumerated serial port. This is the Cortex®-M4's serial console. Set the speed to 115200 bit/s, data bits 8, no parity, and power on the board.
-
Power up the board and stop the boot process by pressing any key before the U-Boot countdown reaches zero. At the U-Boot prompt on the first terminal emulator, type the following commands to U-Boot.
123
=> fatload mmc 1:1 0x88000000 hello_world.bin => dcache flush => bootaux 0x88000000
External Memory
External Memory
| Documents and Videos | Description |
|---|---|
| i.MX 8/8X Family DDR Tools Release |
The purpose of the i.MX 8/8X DDR Tools is to enable users to generate and test a custom DRAM initialization based on their device configuration (density, number of chip selects, etc.) and board layout (data bus bit swizzling, etc.). |
Security and Integrity
| Documents and Videos | Description |
|---|---|
| AN12714 i.MX Encrypted Storage Using CAAM Secure Keys |
Provides the steps to run a transparent storage encryption at block level using DM-Crypt taking advantage of the secure key feature provided by i.MXs Cryptographic Accelerator and Assurance Module (CAAM) |
| AN12838 Strengthening Public Key Cryptography using CAAM Secure Key |
Describes the public key cryptography scheme based on the Black Key feature provided by the i.MX application processors. |
| AN12554 Demo Application to Generate Red/Black Blobs Using CAAM and Encrypt/Decrypt Data |
Instructions and steps on how to set up and run a demo application to generate both red and black key blobs and use them to encrypt and decrypt data. |
| AN12906 HSM and SHE on i.MX 8QXP and i.MX 8DXL |
Hardware Secure Module (HSM) and Secure Hardware Extension (SHE) are two security services for NXP products, that supports in various types of automotive applications. This document provides an initial knowledge of the architecture of these services and helps to develop an application using the HSM and SHE APIs. |
| Trusted Execution Environment: Getting Started with OP-TEE on i.MX Processors |
An overview of TEE, example use cases and how to leverage i.MX hardware security features from OP-TEE. |
| Secure the Edge: Manufacturing Protection: Provision Sensitive Material in an Unsecure Environment |
This webinar will provide an introduction to the Manufacturing protection feature and discuss how it can be used to ensure that sensitive material is delivered and installed securely. |
| AN12312 Secure Boot on i.MX 8 and i.MX 8X Families using AHAB |
The i.MX family of applications processors provides this capability with the Advanced High Assurance Boot (AHAB) component on the on-chip ROM and the Security Controller (SECO) Firmware. The AHAB in ROM is responsible for authenticating the SECO firmware (NXP signed), which will supply the services for authenticating the images signed by the user to the System Controller ROM. |
| AN12812 Using Code-Signing Tool with Hardware Security Module |
This document provides the information necessary for the user to effectively use Code-Signing Tool (CST) with a Hardware Security Module (HSM) backend. |
CAAM Module Example
The i.MX 8XLite EVK board includes the Cryptographic Acceleration and Assurance Module (CAAM) module that can be used through CryptoDev in order to accelerate by hardware the encryption and decryption process. It is recommended to use this module when working with large amounts of data or in any application where performance is important. This example shows the advantages of using CAAM as an encryption offload engine.
Checking the Speed Performance
OpenSSL is an open source project that defines the security protocols SSL (Secure Sockets Layer) and TLS (Transport Layer Security). It has a software library that can be used in applications that require a secure information transmission in order to prevent eavesdropping.
OpenSS includes a speed command that tests the encryption performance for a desired encryption algorithm. For this example, the algorithm used is the aes-128-cbc that implements the Advanced Encryption Standard (AES) encryption algorithm, with a Cipher Block Chaining (CBC) mode of operation and 128 bits block.L
The OpenSSL speed test can be seen using the following command:
1234567891011121314151617# openssl speed -evp aes-128-cbc
Doing aes-128-cbc for 3s on 16 size blocks: 19785933 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 64 size blocks: 10656521 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 256 size blocks: 3706151 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 1024 size blocks: 1036434 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 8192 size blocks: 134183 aes-128-cbc's in 3.00s
OpenSSL 1.0.2n 7 Dec 2017
built on: reproducible build, date unspecified
options:bn(64,32) rc4(ptr,char) des(idx,cisc,16,long) aes(partial) idea(int)
blowfish(ptr)
compiler: arm-poky-linux-gnueabi-gcc -march=armv7ve -mfpu=neon -mfloat-abi=hard
-mcpu=cortex-a7
-DL_ENDIAN -DTERMIO -O2 -pipe -g -feliminate-unused-debug-types -Wall -Wa,--noexecstack
-DHAVE_CRYPTODEV
-DUSE_CRYPTODEV_DIGESTS The 'numbers' are in 1000s of bytes per second processed. type
16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes aes-128-cbc 105524.98k 227339.11k
316258.22k 353769.47k 366409.05kLoad the cryptodev module and run the openssl command again. This time you should be able to see that the timing values show the accelerated values. As the block sizes increases, the elapsed time decreases:
123456789101112131415# modprobe cryptodev
cryptodev: driver 1.9 loaded.
# openssl speed -evp aes-128-cbc -engine cryptodev engine "cryptodev" set.
Doing aes-128-cbc for 3s on 16 size blocks:
103333 aes-128-cbc's in 0.07s Doing aes-128-cbc for 3s on 64 size blocks: 102441
aes-128-cbc's in 0.09s
Doing aes-128-cbc for 3s on 256 size blocks: 84088 aes-128-cbc's in 0.08s
Doing aes-128-cbc for 3s on 1024 size blocks: 72447 aes-128-cbc's in 0.04s
Doing aes-128-cbc for 3s on 8192 size blocks: 25304 aes-128-cbc's in 0.03s OpenSSL
1.0.2n 7 Dec 2017 built on: reproducible build, date unspecified options:bn(64,64)
rc4(ptr,char) des(idx,cisc,16,int) aes(partial) idea(int) blowfish(ptr) compiler:
aarch64-poky-linux-gcc -DL_ENDIAN -DTERMIO -O2 -pipe -g -feliminate-unused-debug-type
The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256
bytes 1024 bytes 8192 bytes aes-128-cbc 23618.97k 72846.93k 269081.60k 1854643.20k
6909678.93kThe encryption algorithms supported by the CryptoDev can be listed by the following command:
1234# openssl engine cryptodev -c
(cryptodev) BSD cryptodev engine
[RSA, DSA, DH, DES-CBC, DES-EDE3-CBC, AES-128-CBC, AES-192-CBC, AES-256-CBC,
hmacWithMD5, hmacWithSH A1, RIPEMD160, MD5, SHA1]Tools and References
Security Reference Manual for i.MX 8DualXLite/8SoloXLite Application Processors
Wired Communications
| Documents and Videos | Description |
|---|---|
| AN12409 i.MX6/7/8 series USB Certification Guide |
The purpose of this document is to describe how to perform USB Certification Test on the i.MX6/7/8 series family of applications processor including procedure descriptions, tools and criteria for USB Compliance Test. |
| AN12444 PCIe Certification Guide for i.MX 8 Series |
A fast and easy way to describe the compliance test procedures, tools, and criteria for PCI Express 3.0, 2.0, and 1.1/1.0a designs on i.MX 8 series products for both silicon validation, as per the PCIe® BASE specification and add-in cards motherboard systems, as per the PCIe CEM specification. |
| AN13164 i.MX8MP PCIe Bandwidth Analysis |
This document presents various usage scenarios for PCIe on the i.MX 8M Plus to provide a more clear understanding of the cases where near Gen3 x1 line rate bandwidth (8 Gbits/s) can be achieved after protocol overhead. |
| AN13210 How to Use FlexCAN in Linux |
i.MX 8MP EVK - i.MX8MP presents two FlexCAN FD interfaces which can be programmed from Realtime domain or Linux domain. This document presents various usage scenarios for FlexCAN on the i.MX 8M Plus to provide a clearer understanding of how FlexCAN to be used in Linux. |
Connectivity
To connect to the Internet on Linux with i.MX 8XLite EVK follow the steps below:
- Connect an Ethernet cable to the board
RJ-45connector. - Boot up the board and wait for the Linux prompt.
- At the Linux prompt, enter the following command.
1
# ifconfig eth0 -
Ping any site to corroborate functionality.
123456
# ping 8.8.8.8 PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data. 64 bytes from 8.8.8.8: icmp_seq=1 ttl=119 time=4.81 ms 64 bytes from 8.8.8.8: icmp_seq=2 ttl=119 time=4.87 ms 64 bytes from 8.8.8.8: icmp_seq=3 ttl=119 time=4.94 ms 64 bytes from 8.8.8.8: icmp_seq=4 ttl=119 time=4.61 ms
Wireless Connectivity
Wireless Connectivity
| Documents and Videos | Description |
|---|---|
| Cloud Connectivity |
Integrated support for cloud services including Amazon Web Services, Microsoft Azure and Google Cloud IoT. |
| Getting Started with NXP-based WiFi modules on i.MX 8M Quad EVK Running Linux OS |
This manual covers the bring-up of i.MX 8M Quad EVK, configurations for the BSP image, hardware connection with NXP-based wireless modules, and how to bring up the Wi-Fi and Bluetooth interfaces. |
| Feature Configuration Guide for NXP-based Wireless Modules on i.MX 8M Quad EVK |
This document specifies the Wi-Fi/Bluetooth features and configurations on i.MX 8M Quad EVK with Azurewave AW-CM358MA (88W8987) and Azurewave AW-CM276MA (88W8997) wireless modules. It covers the initialization and configuration of the Wi-Fi and Bluetooth interfaces. |
Multicore and Hardware Acceleration
Multicore and Hardware Acceleration
| Documents and Videos | Description |
|---|---|
| AN13285 i.MX 8X Using L1 Cache for Cortex-M4 Core |
Introduces the basic technology of the cache system including the L1 cache, memory types, attributes, and Memory Protection Unit for the Cortex-M4 core embedded into the i.MX 8X series processors. It guides you on how to use the cache to develop applications running correctly and with high performance |
Power Management
The PF8100-8200 are the NXP Power Management ICs optimized for i.MX 8 and i.MX8X families.
| Documents and Videos | Description |
|---|---|
| i.MX Power Measurement Tool |
Illustrates the current drain measurements of the i.MX 8XLite application processors taken on the NXP to Evaluation Kit (EVK) platform through several use cases. |
Low Power Mode Suspension Example
With Linux running on the i.MX board, you can evaluate special features that i.MX SoCs provide. This example shows how to suspend to low-power modes and resuming to normal operation.
- Enter the command below in order to enable serial TTY as a wake up source for the board:
1
# echo enabled > /sys/class/tty/ttymxc0/power/wakeup -
Enter the command below to enter Suspend-To-RAM mode:
12345
# echo mem > /sys/power/state [ 18.832439] PM: Syncing filesystems ... done. [ 18.939268] Freezing user space processes ... (elapsed 0.001 seconds) done. [ 18.947957] Freezing remaining freezable tasks ... (elapsed 0.001 seconds) done. [ 18.956810] Suspending console(s) (use no_console_suspend to debug) -
Press the
SW3switch to wake-up the board. The following messages should appear on terminal:123456789101112131415161718192021222324252627282930313233
[ 138.859067] PM: suspend of devices complete after 40.103 msecs [ 138.859071] PM: suspend devices took 0.040 seconds [ 138.861306] PM: late suspend of devices complete after 2.229 msecs [ 138.864518] PM: noirq suspend of devices complete after 3.207 msecs [ 138.864521] Disabling non-boot CPUs ... [ 138.892702] CPU1: shutdown [ 138.892705] psci: CPU1 killed. [ 138.940761] CPU2: shutdown [ 138.940764] psci: CPU2 killed. [ 138.992702] CPU3: shutdown [ 138.992704] psci: CPU3 killed. [ 139.005413] Enabling non-boot CPUs ... [ 139.017625] Detected VIPT I-cache on CPU1 [ 139.017647] GICv3: CPU1: found redistributor 1 region 0:0x00000000388a0000 [ 139.017689] CPU1: Booted secondary processor[410fd034] [ 139.018002] cache: parent cpu1 should not be sleeping [ 139.018221] CPU1 is up [ 139.033610] Detected VIPT I-cache on CPU2 [ 139.033624] GICv3: CPU2: found redistributor 2 region 0:0x00000000388c0000 [ 139.033654] CPU2: Booted secondary processor [410fd034] [ 139.033930] cache: parent cpu2 should not be sleeping [ 139.034129] CPU2 is up [ 139.049722] Detected VIPT I-cache on CPU3 [ 139.049737] GICv3: CPU3: found redistributor 3 region 0:0x00000000388e0000 [ 139.049767] CPU3: Booted secondary processor [410fd034] [ 139.050049] cache: parent cpu3 should not be sleeping [ 139.050257] CPU3 is up [ 139.106888] PM: noirq resume of devices complete after 56.624 msecs [ 139.108600] PM: early resume of devices complete after 1.408 msecs [ 139.115589] Suspended for 0.435 seconds [ 139.116781] PM: resume of devices complete after 8.175 msecs [ 139.262945] Restarting tasks ... done. [ 139.277327] hantro receive hot notification event: 0
Minicom Tutorial
Serial Communication Console Setup
On the command prompt of the Linux host machine, run the following command to determine the port number:
1$ ls /dev/ttyUSB*Four new ports should be exposed. The third one is for Arm® Cortex®-A35 core and the second one is for Arm Cortex-M4 core.
Minicom
Use the following commands to install and run the serial communication program (minicom as an example):
- Install Minicom using Ubuntu package manager.
1
$ sudo apt-get install minicom - Launch Minicom using a console window using the port number determined earlier.
1
$ sudo minicom /dev/ttyUSB* -s - Configure Minicom as show in Figure 3

Tera Term Tutorial
Serial Communication Console Setup
The FTDI USB-serial chip on i.MX 8DualXLiteenumerates four serial ports. Assume that the ports are COM10 to COM13. The third numbered port COM12 is for the serial console communication from Arm Cortex-A35 core and the second numbered port COM11 is for Arm Cortex -M4 core. The serial-to-USB drivers are available FTD Chip Drivers
Tera Term
Is an open source terminal emulation application. This program displays the information sent from the NXP development platform’s virtual serial port.
- DownloadTera Term. After the download, run the installer and then return to this webpage to continue.
- Launch TeraTerm. The first time it launches, it shows the following dialog. Select the serial option. Assuming your board is plugged in, there should be a COM port automatically populated in the list.
- Configure the serial port settings (using the
COMport number identified earlier) to115200baud rate,8data bits, no parity and1stop bit. To do this, go to Setup → Serial Port and change the settings. - Verify that the connection is open. If connected, Tera Term shows something like below in its title bar.

PuTTY Tutorial
Serial Communication Console Setup
The FTDI USB-serial chip on i.MX 8DualXLite enumerates four serial ports. Assume that the ports are COM10 to COM13. The third numbered port COM12 is for the serial console communication from Arm Cortex-A35 core and the second numbered port COM11 is for Arm Cortex -M4 core. The serial-to-USB drivers are available at
FTD Chip Drivers
PuTTY is a popular terminal-emulation application. This program displays the information sent from the NXP development platform’s virtual serial port.
- Download PuTTY After the download, run the installer and then return to this webpage to continue.
- Launch PuTTY by either double clicking on the executable file you downloaded or from the Start menu, depending on the type of download you selected.
- Configure In the window that launches. Select the Serial radio button and enter the
COMport number that you determined earlier. Also enter the baud rate, in this case115200.
- Click Open to open the serial connection. Assuming the board is connected and you entered the correct
COMport, the terminal window opens. If the configuration is not correct, PuTTY alerts you.
Support
Troubleshooting
Demo not working?
Did your board come in a box that looks like this?

No problem! Your board simply came in the old packaging and has a different out-of-box demo loaded into the flash memory.
You should be seeing the red and green LEDs toggling back and forth. It's OK to move onto the next step when you're ready
Still not Working?
Try proceeding to the next steps to get other example applications running on your board. If you still have problems, try contacting us through the NXP Community.
Training
To learn what to do next, find your issue below. If you still need help, contact NXP Support.
| Training | Description |
|---|---|
| AN13273 i.MX 8QuadXPlus/8DualXPlus/DualX Product Lifetime Usage | Describes the estimated product lifetimes for the i.MX 8QuadXPlus/8DualXPlus/8DualX application processors based on the criteria used in the qualification process. |
| I.MX 8X Training | Full list of on-demand training, how-to videos and webinars from NXP about this product. |
Communities
Connect with other engineers and get expert advice on designing with the i.MX8X on one of our community sites.
- i.MX Forums
- Useful Documents and Threads of i.MX Processors
- i.MX Solutions
- Power Management
- Wireless Connectivity
Software Forums