Discussions around embedded security typically focus on risks incurred after a
device is deployed in the field. Those discussions are valid, but security
issues typically start much earlier in the product lifecycle. No matter what
sort of device you are investing in it is increasingly important to pay
attention to security from the start.
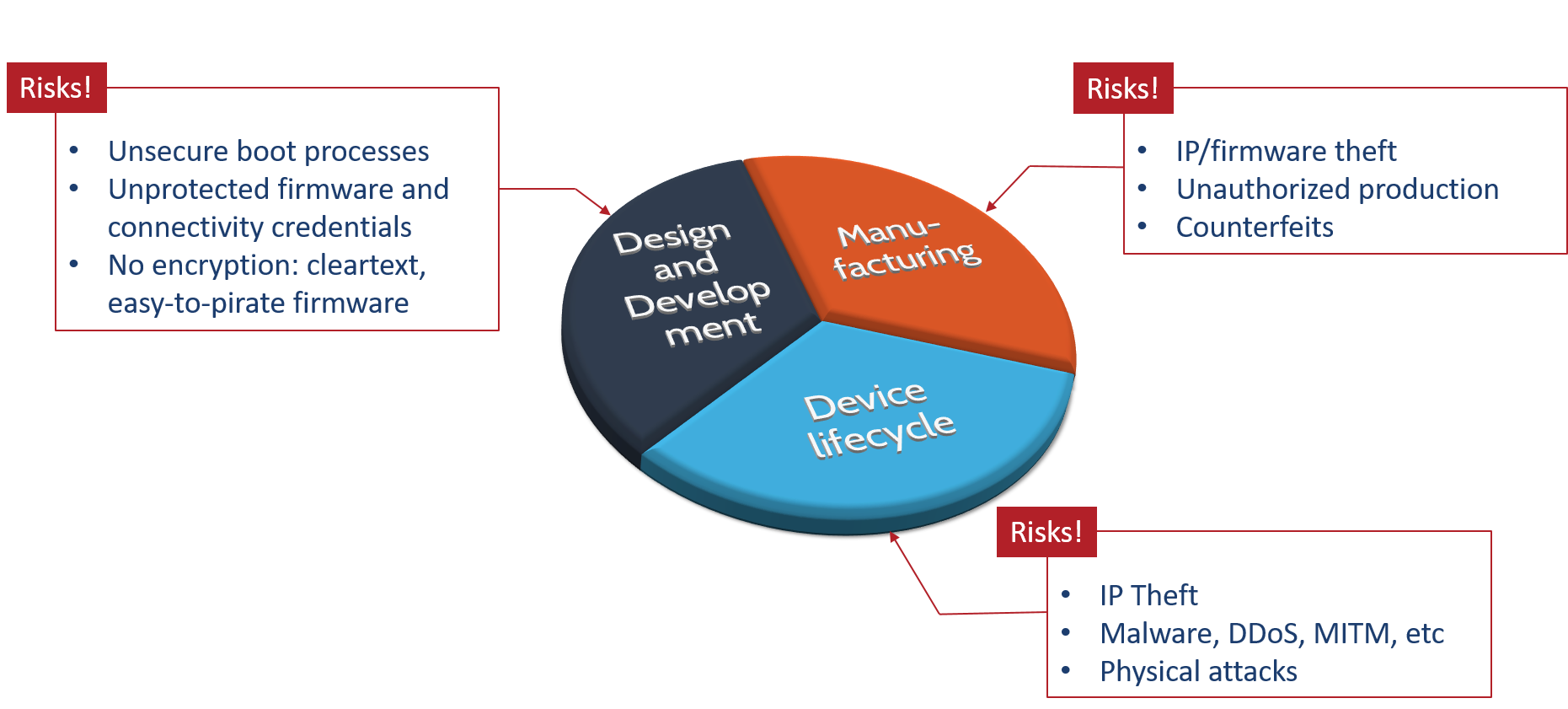
Comprehensive Approach to Embedded Security
For example; some reports state
that nearly half of embedded projects do not encrypt their firmware. This is
compounded by not having secure boot processes or leaving key credentials
(when they exist) unprotected. This leads to more risks incurred during
manufacturing where firmware theft is commonplace leading unauthorized cloning
and in turn loss of revenue, competitiveness and intrinsic business value.
It also leads to connected products or devices that are
defenseless to cyber-attacks focused on IoT devices such as cameras, listening
devices, embedded computers, gateways, washing machines, refrigerators or
smart TVs. In fact, almost any modern appliance will contain Internet
connected embedded processors and therefore should carry an automatic
requirement of embedded security.
While techniques to avoid these sorts of problems have existed for many years,
few device developers make use of them. Why? Well a common reason
is that the developers are unaware of the capabilities of modern SoC devices
to protect their intellectual property, related to this is the fact that even
if they are aware of the security features on the devices they don’t
have the time or experience to implement the feature in their systems.
The good news is that there are now companies who have the expertise and are
offering solutions to help device developers quickly implement trusted and
encrypted firmware to both protect the intellectual property of the product
developer, but also to secure the data and communications of the users of the
device.
Sequitur Lab’s is a leading example of a company that has made it its
mission to secure embedded systems. Sequitur’s EmSPARK Security
Suite is a product that addresses this multi-faceted problem head-on with a
solution that automates the deployment of a security platform and delivers an
abstraction to help simplify making use of the Trust Architecture components
included on all NXP processors.
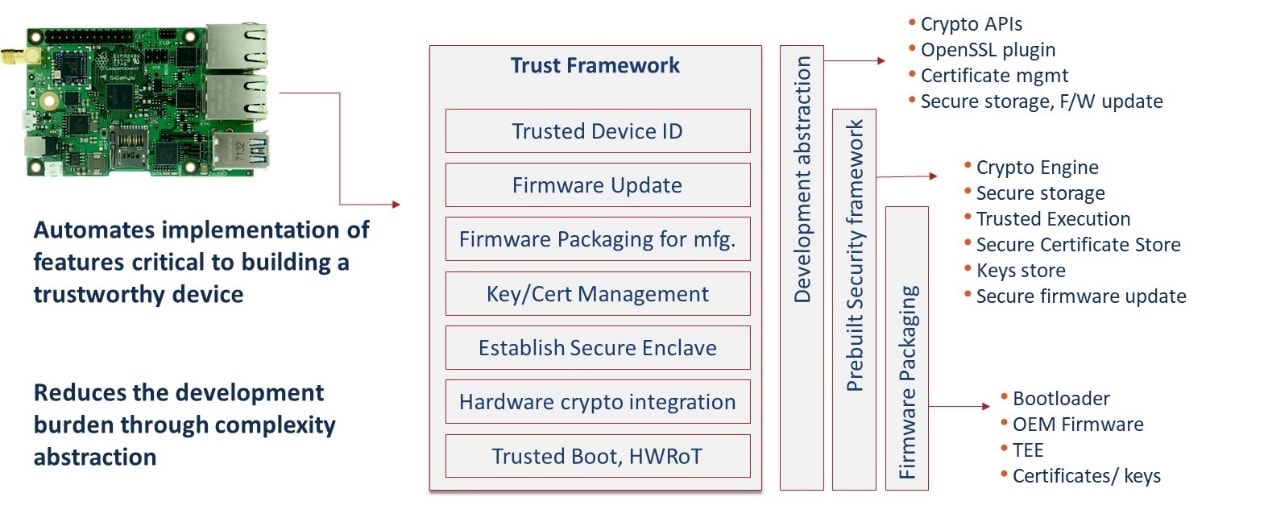
EmSPARK Suite Features
The Suite establishes a security platform including
-
Extended secure boot processes beyond initial ROM boot to validating and
launching a signed copy of the Rich OS (Linux, VxWorks, Etc.).
-
Implementing security critical services such as initializing a secure
enclave to enable trusted execution.
- Trusted ID bound to a hardware root of trust.
- Secure firmware update process
- Essential key and certificate management services
- Firmware preparation for volume manufacturing
Benefits
Customers committed to the Layerscape and or i.MX platforms can standardize on
a security approach for a broad variety of device types without having to
invest time and effort in becoming security experts on each platform.
Sequitur’s EmSPARK Security Suite simplifies developers lives in
two ways – (1) the packaged, preconfigured set of security functions
eliminates the need to build these from scratch and (2) the included Linux
APIs that allows them to rapidly make use of the security functions and
capabilities.
Security at Scale
Implementing device security is one challenge but provisioning devices during
manufacturing with the security platform and relevant customer secrets (keys
and certificates) is an equally big challenge. Without the right tools and
processes, product developers risk losing control over their intellectual
property and incur loss of revenue through piracy. EmSPARK provides tools and
processes for firmware preparation that makes it possible to manufacture
devices in untrusted facilities without risking theft of firmware or
unauthorized manufacturing of devices.
Sequitur will work closely with companies and their manufacturing partners to
ensure secure device provisioning within existing manufacturing workflows.
Sequitur Labs, recently announced the general availability of EmSPARK Security
Suite for NXP’s Layerscape and i.MX line of microprocessors.
NXP’s Trust Architecture brings comprehensive hardware security
capabilities for building secure products. Trust Architecture brings hardware
crypto acceleration, secure key store, secure isolated domain aka ARM®
TrustZone processor security technology among other features as essential
underpinnings for securing IoT driven digital transformation.
Sequitur’s EmSPARK Suite extends NXP’s Trust Architecture into
the application runtime while dramatically reducing the cost and effort
required to do so. EmSPARK achieves this while maintaining the uniqueness of
each processor’s security features, meaning that the EmSPARK Suite is
preconfigured to take advantage of hardware security features of Trust
Architecture for each processor family and variants within a family.
If you are developing with NXP Layerscape or i.MX application processors and
were wondering what you can to do build a more secure device, please consider
connecting with Sequitur Labs (www.sequiturlabs.com). They will open
your eyes to both the necessity of using the trust capabilities of the NXP
processors but also how easy it can be with the help of an expert partner.






